The Salesforce platform enables the development of multiple use cases, applications, and services to manage your customer data. But this flexibility can lead to vulnerabilities if the security of access to it is not completely guaranteed.
Data protection plays a vital role for organizations, not taking it seriously can lead to fatal consequences. To enhance security and guarantee the integrity of your organization’s information, Salesforce offers you a series of functionalities, measures and tools that we have condensed into a list of the 10 best security practices. Below, we are sharing each of them:
1- Activate multi-factor authentication (MFA).
MFA is a secure authentication method that requires users to prove their identity by providing two or more pieces of evidence when they log in. One factor may be your username and password. Another factor may be the use of security keys or authentication applications. These authenticator apps create unique login codes for a more secure authentication process. It also has biometric authentication for the case of mobile devices. Among the most common are fingerprint scanning and facial recognition.
2- Restrict access by using IP ranges.
Salesforce works on a multi-tenant architecture, where resources are shared between users with privacy and security. To ensure that only authorized users can access your organization, administrators can restrict access by using IP ranges. These limit access by requiring users to log in to Salesforce from designated IP addresses, typically from your corporate network or VPN.
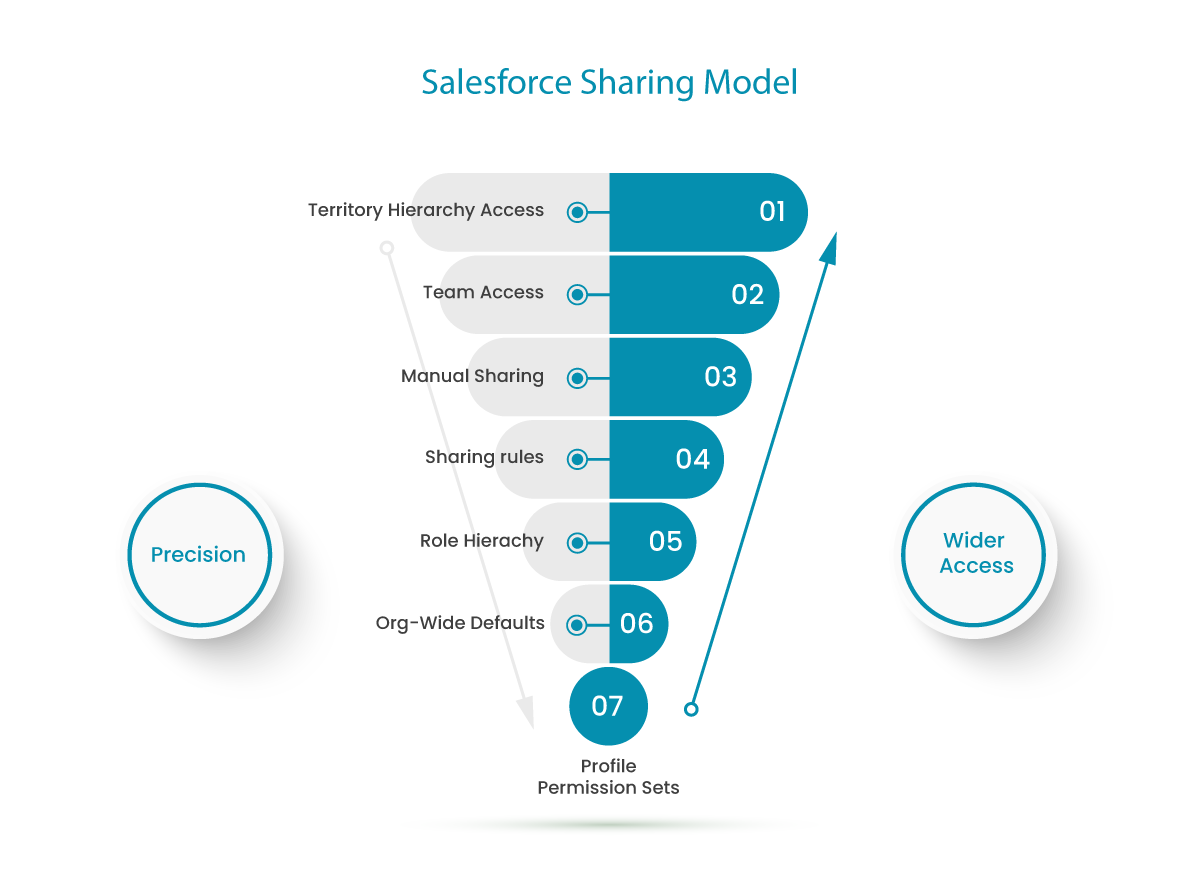
3- Apply granular access control using profiles and permission sets.
To grant users access to your data, Salesforce recommends using profiles and permission sets. Profiles define what operations users can do and what objects or data they can access. When you create users, you assign a profile to each one. The use of profiles can sometimes lead to providing types of access that are not necessary for some users. Instead, permission sets can be used as a more refined solution. With them, the functional access of the users is extended, without changing their profiles by allowing them to assign extra permissions. Profiles and permission sets are very flexible, but if not managed properly, they can be a huge risk to your data security. To do this, the administrator must provide access to view and edit sensitive information to only a small group of authorized employees.
4- Establish secure password management policies.
- A strong password must contain a combination of alphanumeric characters that includes the combination of upper and lower case letters and the use of symbols. It must also have a minimum length between 8 and 10 characters.
- Salesforce recommends to set the user passwords expiration for 90 days after they are created.
- Enforce password history. This ensures that the new password does not match any of the last 5 previously used passwords.
5- Limit the number of failed logins.
Set a maximum of 3 possibilities when trying to log in by entering the wrong password.
6- Force session reboot when a user is inactive.
When the session times out, the session will expire. To continue working, the user must log in again.
7- Run checks on your organization’s security status.
To check the configuration of your organization’s security features, Salesforce offers you the standard and free tool Health Check. This tool allows administrators to manage your company’s most important security settings from a single panel.
Health Check covers everything from password policy configuration to session management and file management. These checks generate a percentage assessment of your organization’s level of security. For example, less than 54% is considered very poor and excellent above 90%. The score is calculated by measuring how closely your organization’s security settings match those recommended by Salesforce.
8- Evaluate the use of the Salesforce Shield.
For organizations that need to meet additional security requirements, Salesforce has the payment tool Salesforce Shield. It is amount to of three security tools: Shield Platform Encryption, Event Monitoring, and Field Audit Trail.
Shield Platform Encryption, is much more complex and deeper than classic Salesforce encryption. It would allow you to encrypt a variety of widely used standard fields, along with some custom fields. Classic Salesforce encryption only allows you to protect a special type of custom text field that is created for that purpose.
Real-time event monitoring gives you access to detailed performance, security, and usage data across all your Salesforce apps.
Field audit trail allows you to know, at any time, the status and value of your data on any date. It maintains the record of all kinds of modifications concerning administration, personalization, security and data management. Salesforce includes some level of field history tracking by default. Salesforce Shield allows you to extend this tracking by expanding this field history from 6 months to 10 years. This can be especially useful for regulated industries, such as healthcare and government agencies, that need to maintain extensive audit trails.
9- Regularly generate a new encryption key.
If you use platform encryption, Salesforce recommends that you regularly generate a new encryption key.
10- Carry out regular audits.
Periodic controls and audits will allow you to identify irregular behavior and violations of procedures. In addition, they allow you to track unexpected changes and usage trends.
The Salesforce platform offers sufficient security mechanisms so that users and administrators can carry out their work safely. However, their execution requires joint work between administrators and Salesforce. It is with this purpose that this great company provides the necessary educational resources and tools to help its clients protect their data. It remains on the part of the administrators the responsibility to implement the best possible security in their organization.
The best practices recommended by Salesforce should not be overlooked, as they will help reduce risks that compromise the confidentiality and integrity of your data.
Spare no effort when it comes to security, contact us at hello@theskyplanner.com if you need help.



